- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
FortiADC
FortiADC enhances the scalability, performance, and security of your applications whether they are hosted on premises or in the cloud.
- Fortinet Community
- Knowledge Base
- FortiADC
- Technical Tip: Access load balanced server farm vi...
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
bmeta

Staff
Created on 05-26-2020 02:40 AM Edited on 05-26-2022 08:58 AM By Anonymous
Article Id
190069
Description
This article describes how to access server farm via RDP over SSL VPN Web mode and the Fortinet FortiADC using round robin as load balancing method.
Solution
Network topology.
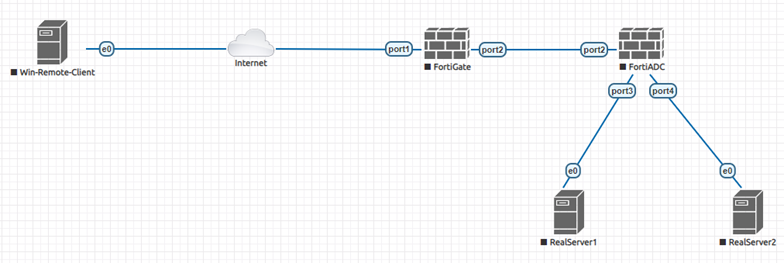
The FortiGate can be configured as VPN gateway.
Create a new authentication group.
Create a new authentication group.
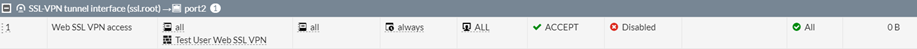
The user has to be member of and set 'web-access' its portal in the SSL VPN settings.
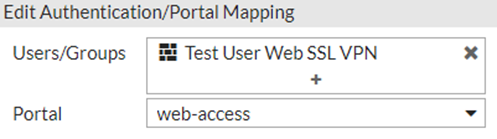
Configure access for the specified group under Policy&Objects.
Setup on the FortiADC.
The traffic flow will be balanced by FortiADC.
There are two real servers configured on POOL_1, and each server has different weight.
For example: weight 1 for 30.30.30.3 and weight 2 for 40.40.40.4.
There are two real servers configured on POOL_1, and each server has different weight.
For example: weight 1 for 30.30.30.3 and weight 2 for 40.40.40.4.
Server load balance topology.
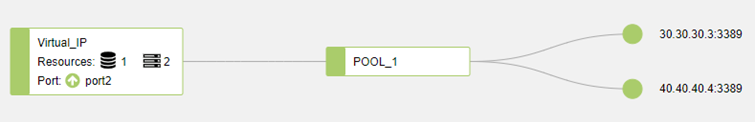
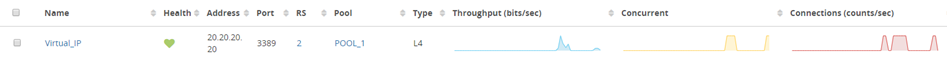
Load Balancing Method: round robin.
Traffic Flow.
Remote User SSL VPN Web Mode -> FortiGate -> FortiADC -> Virtual Server -> Real Server.
FortiGate SSLVPN web portal.
After connecting with the user through SSL VPN Web mode, try to connect to the RDP Virtual Server (20.20.20.20).
Remote User SSL VPN Web Mode -> FortiGate -> FortiADC -> Virtual Server -> Real Server.
FortiGate SSLVPN web portal.
After connecting with the user through SSL VPN Web mode, try to connect to the RDP Virtual Server (20.20.20.20).
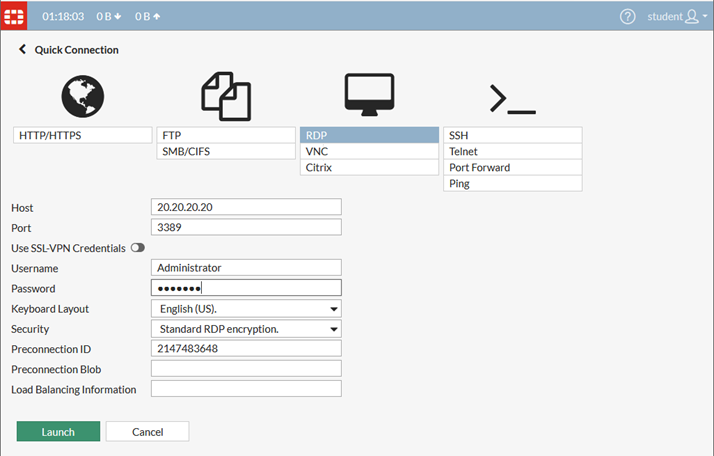
Capture the traffic from the CLI.
# diagnose sniffer packet any "host 20.20.20.20 and port 3389" 4From the FortiADC GUI, monitor this connection with virtual server and destination address.
interfaces=[any]
filters=[host 20.20.20.20 and port 3389]
22.599973 port2 out 20.20.20.1.7267 -> 20.20.20.20.3389: syn 1190583404
22.605683 port2 in 20.20.20.20.3389 -> 20.20.20.1.7267: syn 3383112461 ack 1190583405
22.605714 port2 out 20.20.20.1.7267 -> 20.20.20.20.3389: ack 3383112462
22.605940 port2 out 20.20.20.1.7267 -> 20.20.20.20.3389: psh 1190583405 ack 3383112462
22.612467 port2 in 20.20.20.20.3389 -> 20.20.20.1.7267: psh 3383112462 ack 1190583448
22.612493 port2 out 20.20.20.1.7267 -> 20.20.20.20.3389: ack 3383112473
…..
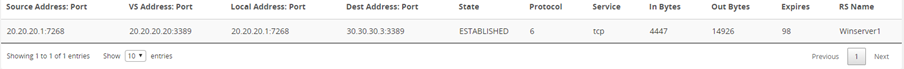
As expected, when another connection attempt is made to the virtual server, FortiADC will show a different destination address.
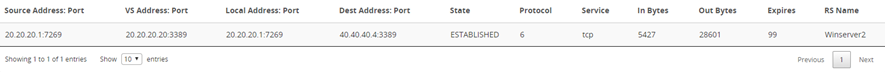
Here, round robin distributes the next new connection to the next server in the pool.
On the FortiGate the debug flow trace will show only the virtual server IP.
Note.
The configuration on FortiGate is straightforward.
Allow the traffic flow under Policy&Objects for SSL VPN connections from the SSL VPN interface to the FortiADC connected interface.
Related link.
https://docs.fortinet.com/document/fortigate/6.2.4/cookbook/579694/ssl-vpn-web-mode-for-remote-user
Note.
On FortiADC double check gateway, DNS, routing & communication toward real servers
On the FortiGate the debug flow trace will show only the virtual server IP.
# diagnose debug flow filter clear
# diagnose debug flow filter addr "20.20.20.20" <----- The virtual servers IP address.
# diagnose debug enable
# diagnose debug flow trace start 3
# id=20085 trace_id=7 func=print_pkt_detail line=5519 msg="vd-root:0 received a packet(proto=6, 20.20.20.1:7272->20.20.20.20:3389) from local. flag [S], seq 2200022367, ack 0, win 42340"
id=20085 trace_id=7 func=init_ip_session_common line=5684 msg="allocate a new session-00001c35"
id=20085 trace_id=8 func=print_pkt_detail line=5519 msg="vd-root:0 received a packet(proto=6, 20.20.20.20:3389->20.20.20.1:7272) from port2. flag [S.], seq 198986456, ack 2200022368, win 64000"
id=20085 trace_id=8 func=resolve_ip_tuple_fast line=5599 msg="Find an existing session, id-00001c35, reply direction"
id=20085 trace_id=8 func=vf_ip_route_input_common line=2591 msg="find a route: flag=84000000 gw-20.20.20.1 via root"
id=20085 trace_id=9 func=print_pkt_detail line=5519 msg="vd-root:0 received a packet(proto=6, 20.20.20.1:7272->20.20.20.20:3389) from local. flag [.], seq 2200022368, ack 198986457, win 6"
id=20085 trace_id=9 func=resolve_ip_tuple_fast line=5599 msg="Find an existing session, id-00001c35, original direction"
Note.
The configuration on FortiGate is straightforward.
Allow the traffic flow under Policy&Objects for SSL VPN connections from the SSL VPN interface to the FortiADC connected interface.
Related link.
https://docs.fortinet.com/document/fortigate/6.2.4/cookbook/579694/ssl-vpn-web-mode-for-remote-user
Note.
On FortiADC double check gateway, DNS, routing & communication toward real servers
Labels:
Broad. Integrated. Automated.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Security Research
Company
News & Articles
Copyright 2024 Fortinet, Inc. All Rights Reserved.