- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Note: How to get log messages for packet...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
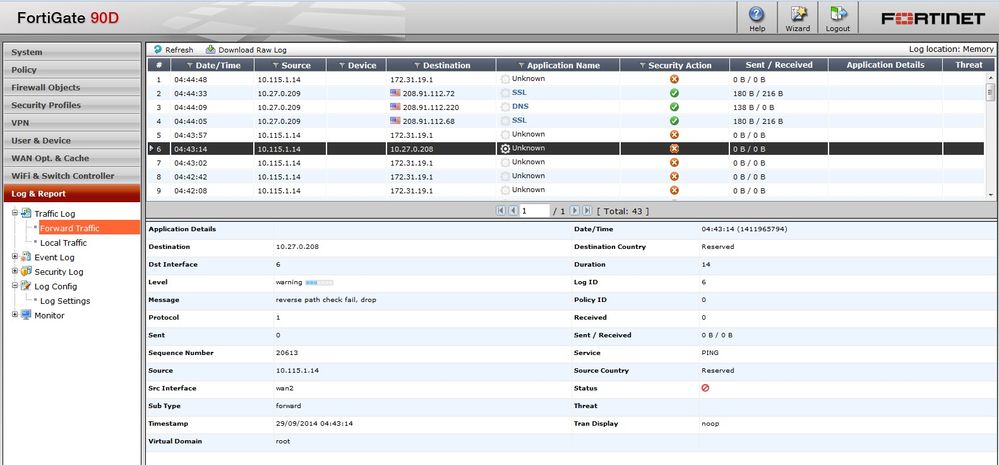
Debug flow shows those drop as “reverse path check fail, drop”.
id=13
trace_id=27 msg="VD1 received a packet(proto=1,
10.11.130.70:1->10.35.252.4:8) from Int1."
id=13 trace_id=27 msg="allocate a new session-086bf186"
id=13 trace_id=27 msg="reverse path check fail, drop"
id=13 trace_id=27 msg="trace"
To help
in troubleshooting and finding incorrect route setting it is
possible to enable logging of any ICMP dropped packets.
The CLI commands are :
config log setting
set log-invalid-packet enable
end
With this option enabled a log message will be logged for "ping" dropped due to anti-spoofing.
Note that this option is not limited to anti-spoofing.
It is a global parameter, independent of traffic log settings.
This setting is not rate limited and a large volume of invalid packets will generate numerous log messages and can affect device performances.
Related Articles
Technical Note: Details about FortiOS RPF (Reverse Path Forwarding), also called Anti-Spoofing
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.