- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
FortiGate
FortiGate Next Generation Firewall utilizes purpose-built security processors and threat intelligence security services from FortiGuard labs to deliver top-rated protection and high performance, including encrypted traffic.
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip : Routing with IP Pool Address Confi...
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
IP Pools are a mechanism that allow sessions leaving the FortiGate Firewall to use NAT.
An IP pool defines a single IP address or a range of IP addresses to be used as the source address for the duration of the session.
These assigned addresses will be used instead of the IP address assigned to that FortiGate interface.
Solution
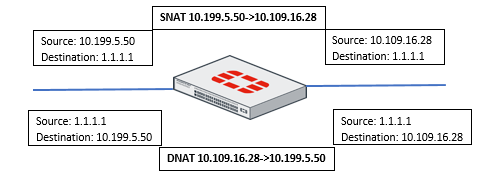
Consider a client having an IP address of 10.199.5.50 and trying to reach destination IP address 1.1.1.1.
IP Pools are a mechanism that allow sessions leaving the FortiGate Firewall to use NAT.
An IP pool defines a single IP address or a range of IP addresses to be used as the source address for the duration of the session.
These assigned addresses will be used instead of the IP address assigned to that FortiGate interface.
Solution
Consider a client having an IP address of 10.199.5.50 and trying to reach destination IP address 1.1.1.1.

An IP pool is configured which is applied to firewall policy ID 1.
When traffic arrives from source IP 10.199.5.50, the traffic will be SNAT to 10.109.16.28.
For return traffic, we will see DNAT happening.
- If the IP Pool address range is created without applying into the Firewall Policy, the IP Pool address range will still be effectively affecting the routing.
- Do not create the IP Pool address range when it is not required to be applied into the Firewall Policy.
- Do not create the IP Pool address range overlap subnet with network interface's IP address.
# config firewall ippoolRunning debug flow will show that traffic is getting SNAT as expected.
edit "10.199.5.50/32"
set type one-to-one
set startip 10.109.16.28
set endip 10.109.16.28
next
end
# config firewall policy
edit 1
set name "internal1-wan1"
set srcintf "internal1"
set dstintf "wan1"
set action accept
set srcaddr "10.199.5.50"
set dstaddr "all"
set schedule "always"
set service "ALL"
set nat enable
set ippool enable
set poolname "10.199.5.50/32"
next
end
id=20085 trace_id=19 func=print_pkt_detail line=5746 msg="vd-root:0 received a packet(proto=1, 10.199.5.50:1->1.1.1.1:2048) from internal1. type=8, code=0, id=1, seq=62."
id=20085 trace_id=19 func=init_ip_session_common line=5918 msg="allocate a new session-007efbe7"
id=20085 trace_id=19 func=vf_ip_route_input_common line=2615 msg="find a route: flag=04000000 gw-10.109.31.254 via wan1"
id=20085 trace_id=19 func=fw_forward_handler line=853 msg="Allowed by Policy-1: SNAT"
id=20085 trace_id=19 func=__ip_session_run_tuple line=3478 msg="SNAT 10.199.5.50->10.109.16.28:1"
For return traffic, we will see DNAT happening.
id=20085 trace_id=20 func=print_pkt_detail line=5746 msg="vd-root:0 received a packet(proto=1, 1.1.1.1:1->10.109.16.28:0) from wan1. type=0, code=0, id=1, seq=62."Important Notes.
id=20085 trace_id=20 func=resolve_ip_tuple_fast line=5827 msg="Find an existing session, id-007efbe7, reply direction"
id=20085 trace_id=20 func=__ip_session_run_tuple line=3492 msg="DNAT 10.109.16.28:0->10.199.5.50:1"
id=20085 trace_id=20 func=vf_ip_route_input_common line=2615 msg="find a route: flag=00000000 gw-10.199.5.50 via internal1"
id=20085 trace_id=20 func=npu_handle_session44 line=1184 msg="Trying to offloading session from wan1 to internal1, skb.npu_flag=00000000 ses.state=00010200 ses.npu_state=0x04000000"
id=20085 trace_id=20 func=fw_forward_dirty_handler line=394 msg="state=00010200, state2=00000000, npu_state=04000000"
- If the IP Pool address range is created without applying into the Firewall Policy, the IP Pool address range will still be effectively affecting the routing.
- Do not create the IP Pool address range when it is not required to be applied into the Firewall Policy.
- Do not create the IP Pool address range overlap subnet with network interface's IP address.
Related Articles
How to NAT an internal mail server to the Internet
Labels:
Broad. Integrated. Automated.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Security Research
Company
News & Articles
Copyright 2024 Fortinet, Inc. All Rights Reserved.