- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
FortiGate
FortiGate Next Generation Firewall utilizes purpose-built security processors and threat intelligence security services from FortiGuard labs to deliver top-rated protection and high performance, including encrypted traffic.
- Fortinet Community
- Knowledge Base
- FortiGate
- Restricting VPN access with two-factor and LDAP au...
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
Restricting VPN access with two-factor and LDAP authentication.
Solution
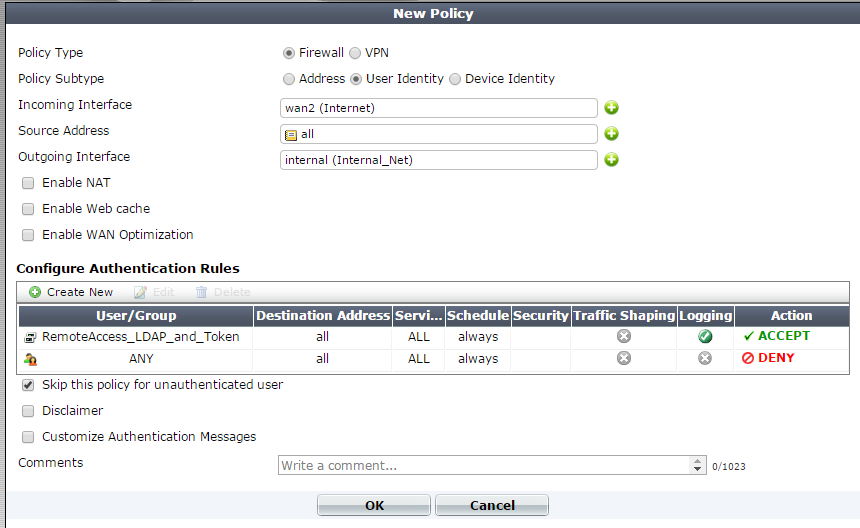
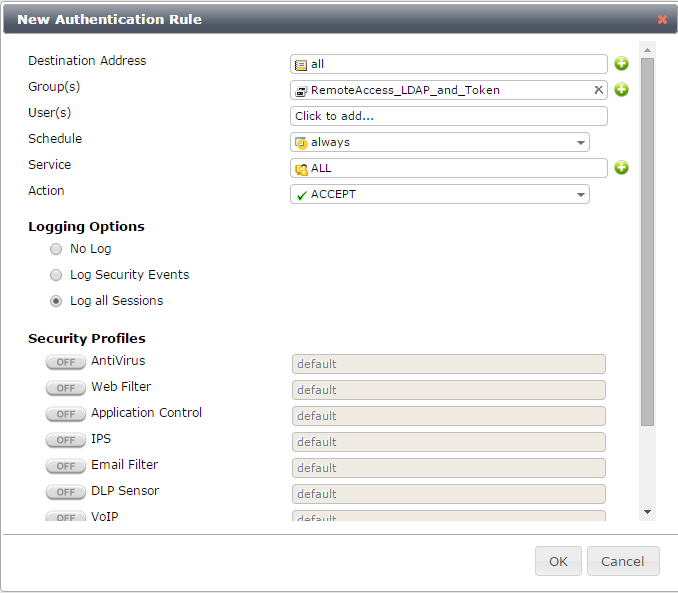
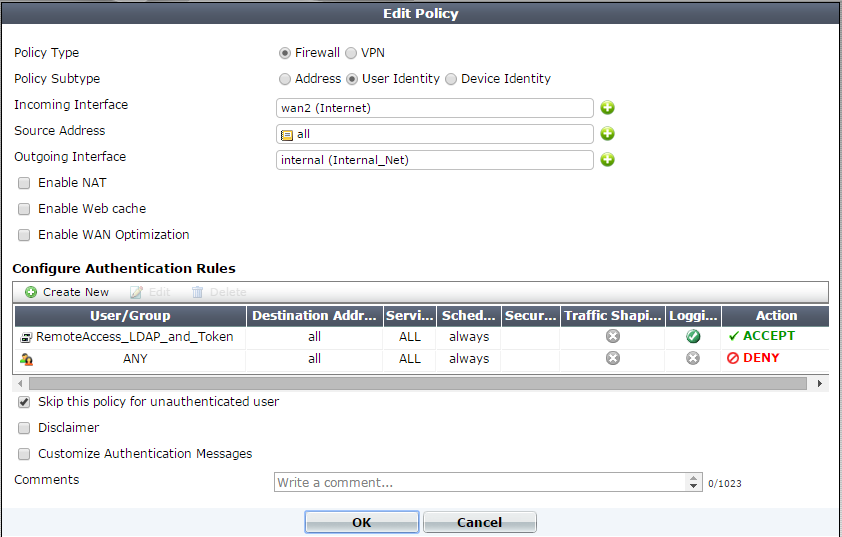
Restricting VPN access with two-factor and LDAP authentication.
Solution
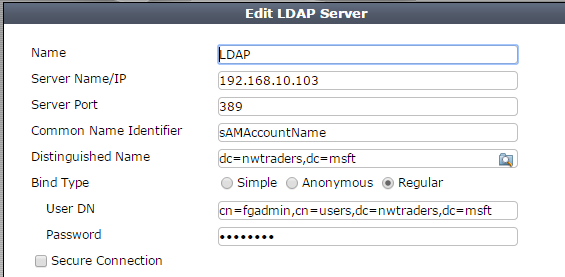
1. Configure FortiGate to LDAP link.

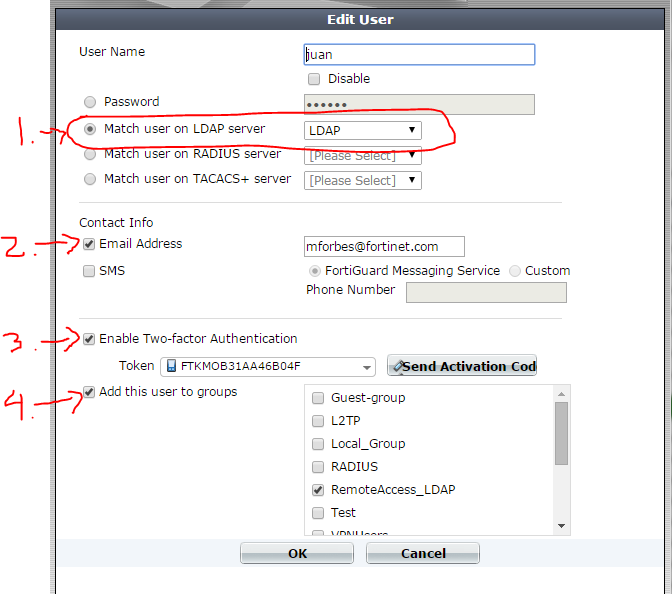
2. Create a 'local' user.
> Create user with same display name as used for LDAP account.
3. Assign a FortiToken to the local user.
> Add the LDAP Server from the drop down list.
> Add an email address if using a Mobile Token. (Needs messenger server setup on FortiGate) (Not available on FortiOS 5.2)
> Enable Two-factor Athentication
> Select Token
> Add user to local Group

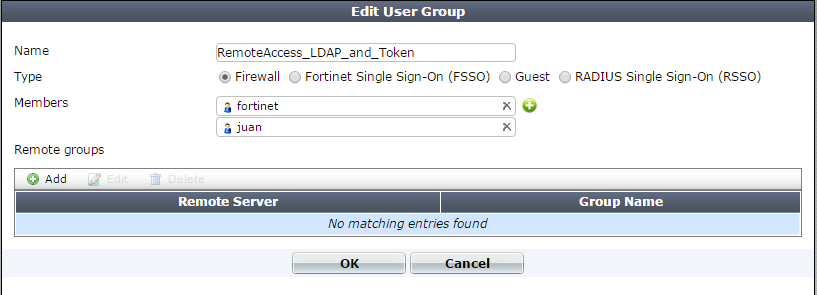
4. Create a User Group.
> Add users that have FortiTokens assigned.
> DO NOT add a 'Remote Group' the the user group.

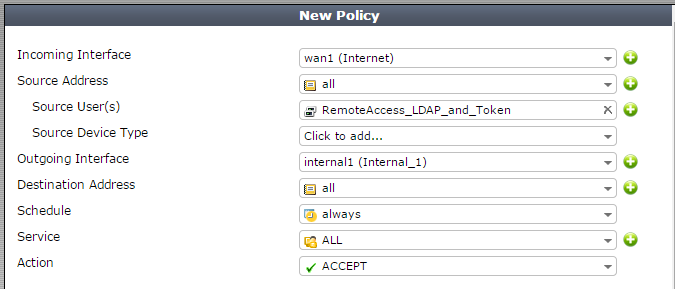
5. Add the 'Remote Access' group to the ssl vpn inbound Policy.
FortiOS 5.2.X
> Create new Firewall Policy
> Under 'Source User(s)', add Add 'RemoteAccess_LDAP_and_Token' group.
> Move firewall Policy to top of list.

FortiOS 5.0.X
> Create a 'User Identity' firewall Policy.
> Add check mark to 'Skip this policy for unauthenticated user'.

> Click 'Create New' under 'Configure Authentication Rules'
> Add the RemoteAccess_LDAP_and_Token local group.
> Do not add any Security Profiles.
> Save Policy.
> Move firewall Policy to top of list.


Labels:
Broad. Integrated. Automated.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Security Research
Company
News & Articles
Copyright 2024 Fortinet, Inc. All Rights Reserved.