- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: How to send logs of VMX Instances t...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on 08-19-2019 01:58 AM Edited on 06-02-2022 09:50 AM By Anonymous
Description
This article describes how to send logs from FortiGate-VMX Instances to FortiAnalyzer.
Solution
FortiGate VMX Instances (notes) can access to outside world only via “sync” interface.
In order to send logs from FortiGate VMX Instances to the FortiAnalyzer, it is require to configure firewall policy on FortiGate SVM in root vdom (management vdom) from sync interface to mgmt interface:
Network diagram:
FortiGate VMX-Instance [sync-10.10.10.2] >>>> [sync-10.10.10.1] FortiGate SVM [mgmt- 10.5.81.21] >>>> [10.5.59.65] FortiAnalyzer
Notes: Before configuring FortiAnalyzer on the FortiGate SVM/VMX Instance, please make sure that there is a connection between FortiGate SVM and FortiAnalyzer.
#config vdom
edit root#config firewall address
edit "FAZ"
set subnet 10.5.59.65 255.255.255.255
next
edit "instance1"
set subnet 10.10.10.2 255.255.255.255
next
end#config firewall policy
edit 2
set name "TO_FAZ"
set srcintf "sync"
set dstintf "mgmt"
set srcaddr "instance1"
set dstaddr "FAZ"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
set fsso disable
set nat enable
next
endCheck connection between FortiGate VMX Instance and FortiAnalyzer:FortiGate-VMX (root) # execute ping 10.5.59.65
PING 10.5.59.65 (10.5.59.65): 56 data bytes
64 bytes from 10.5.59.65: icmp_seq=0 ttl=62 time=1.1 ms
64 bytes from 10.5.59.65: icmp_seq=1 ttl=62 time=1.4 ms
64 bytes from 10.5.59.65: icmp_seq=2 ttl=62 time=1.0 ms
64 bytes from 10.5.59.65: icmp_seq=3 ttl=62 time=1.2 ms
64 bytes from 10.5.59.65: icmp_seq=4 ttl=62 time=0.8 ms
--- 10.5.59.65 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 0.8/1.1/1.4 msGenerate test logs on the FortiGate VMX Instance:
FortiGate-VMX (root) # diagnose log test
generating a system event message with level - warning
generating an infected virus message with level - warning
generating a blocked virus message with level - warning
generating a URL block message with level - warning
generating a DLP message with level - warning
generating an IPS log message
generating an anomaly log message
generating an application control IM message with level - information
generating an IPv6 application control IM message with level - information
generating deep application control logs with level - information
generating an antispam message with level - notification
generating an allowed traffic message with level - notice
generating a multicast traffic message with level - notice
generating a ipv6 traffic message with level - notice
generating a wanopt traffic log message with level - notification
generating a HA event message with level - warning
generating a VOIP event message with level - information
generating authentication event messages
generating a Forticlient message with level - information
generating a URL block message with level - warning
generating a DNS message with level - warning
generating an ssh-command pass log with level - notification
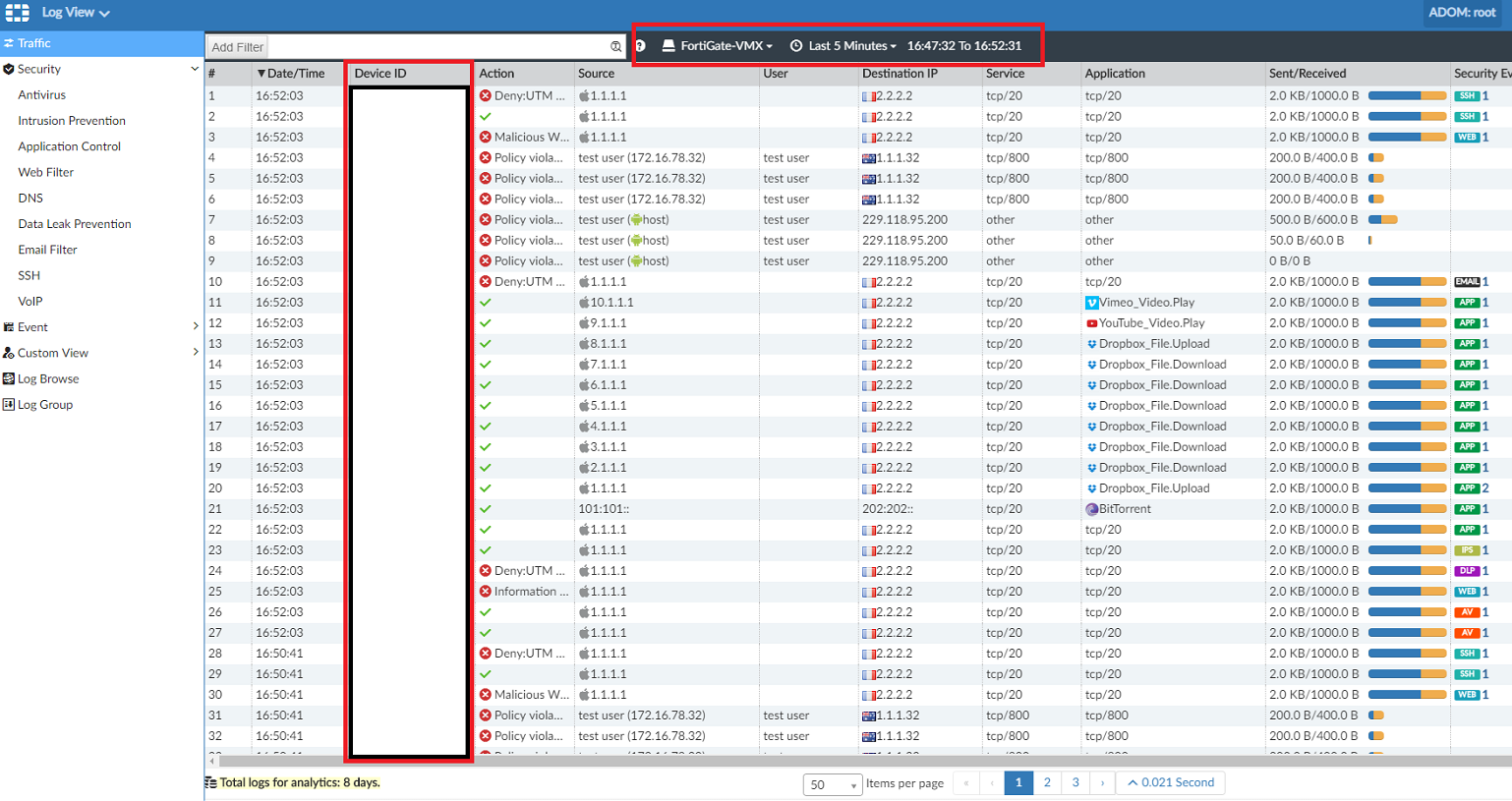
generating an ssh-channel block with level – warningCheck the logs on the FortiAnalyzer:
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.