- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: How to allow a port
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on
09-20-2019
05:05 AM
Edited on
01-31-2024
05:20 AM
By
![]() Jean-Philippe_P
Jean-Philippe_P
Description
This article explains how to allow a port on a FortiGate.
By default, the FortiGate firewall denies all traffic passing through it on all ports due to a pre-configured 'implicit deny policy'.
Scope
FortiGate.
Solution
To allow any traffic through FortiGate on any port, configure the IPv4 policy with the 'action' set to 'Accept/Permit'.
Below is an example of how to allow the RDP port 3389 traffic through FortiGate:
Step 1:
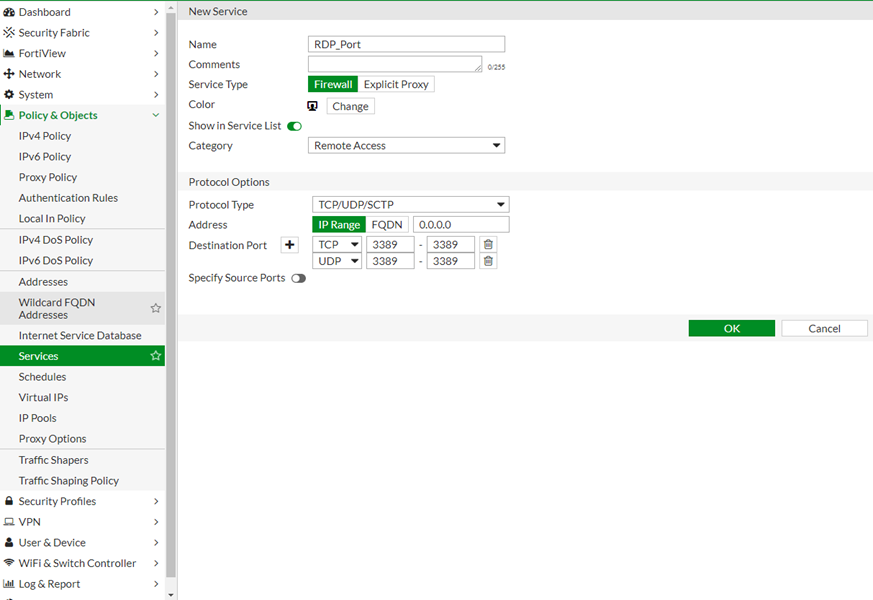
Create the 'Service' Object for port which needs to be allowed under Policy and Object -> Services.
If it is the standard port, there are predefined service objects under 'service list'.
If not, configure the 'Service' Object under Policy and Object -> Services -> Create New -> Service
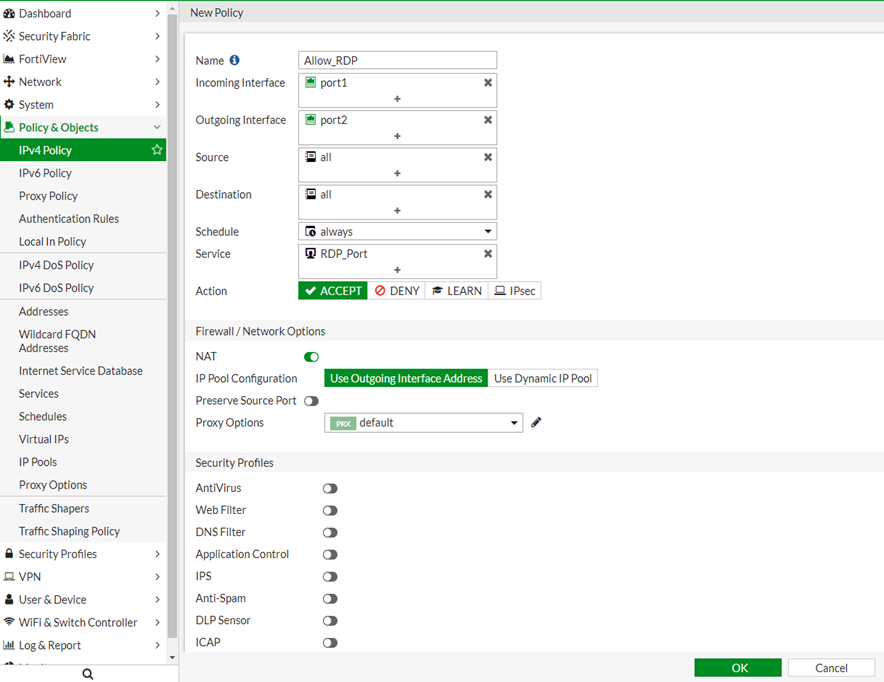
To create a policy, navigate to Policy And Object -> IPv4 Policy -> Create New.
filters=[tcp port 3389 or udp port 3389]
1.427148 port1 in 10.143.3.189.64958 -> 10.5.41.48.3389: syn 2923297620 <- Packet enters on FortiGate Port1 (ingress).
1.427148 port2 out 10.143.3.189.64958 -> 10.5.41.48.3389: syn 2923297620 <- Packet is leaving on port 2 (egress).
Notes:
- Place this specific policy on top of all other general policies.
- If it is required to block the specific port, the steps are the same except with the 'action' set to 'Deny'.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.