- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: Configuring SAML SSO login for SSL ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on
09-29-2020
11:19 AM
Edited on
01-31-2023
08:04 AM
By
![]() Jean-Philippe_P
Jean-Philippe_P
Description
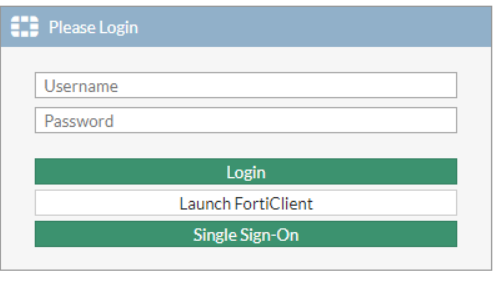
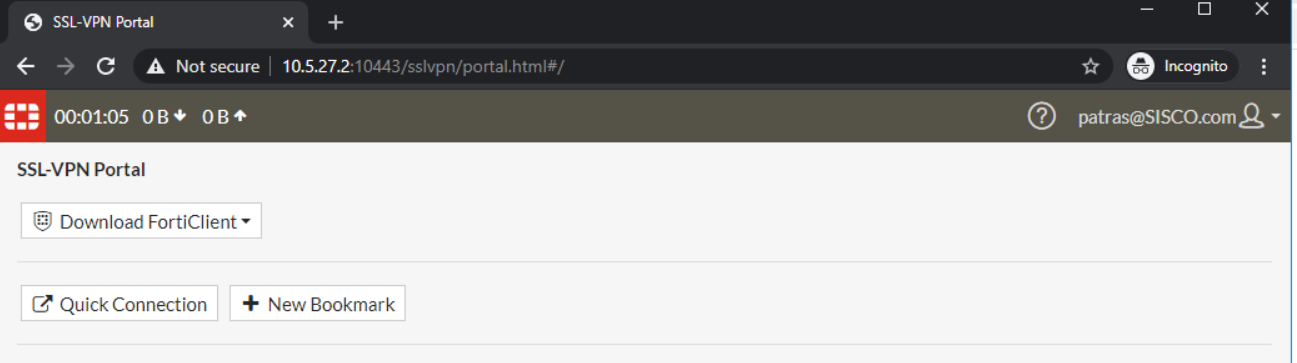
This article describes how to setup both ADFS and FortiGate for SAML SSO for web mode SSL VPN with FortiGate acting as SP.
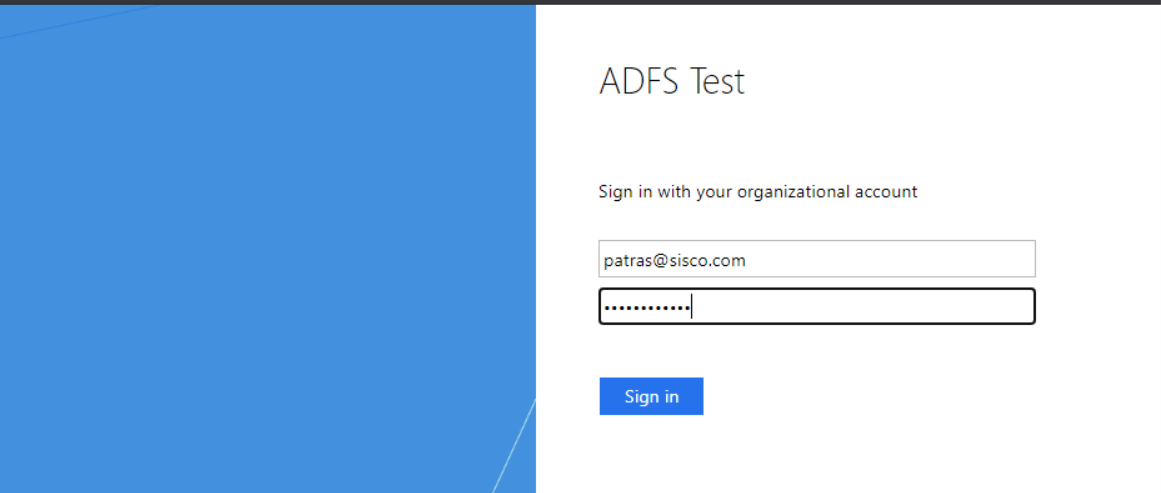
ADFS or Active Directory Federation Service is a feature that needs to install on the AD server separately. Its main purpose is to provide Windows users with Single Sign-On (SSO) access.
Solution
Configuration On Fortigate.
# config user saml
edit "adfs"
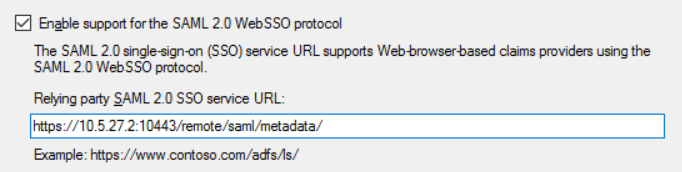
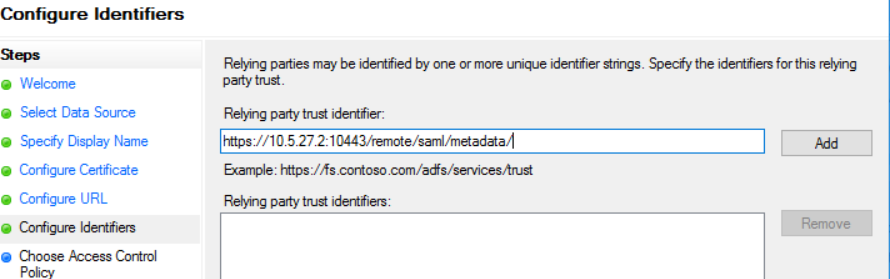
set entity-id "https://10.5.27.2:10443/remote/saml/metadata/"
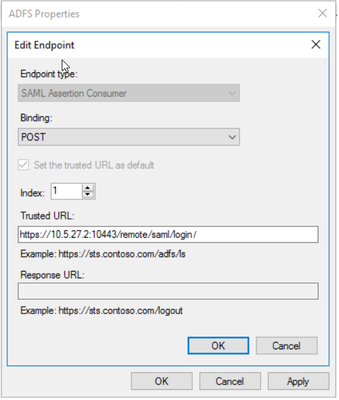
set single-sign-on-url "https://10.5.27.2:10443/remote/saml/login/"
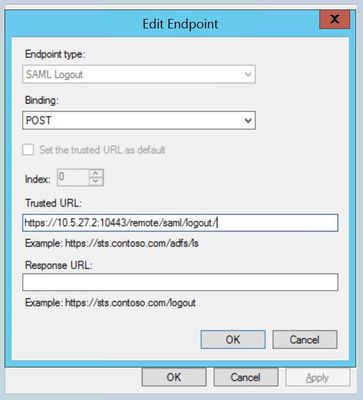
set single-logout-url "https://10.5.27.2:10443/remote/saml/logout/"
set idp-entity-id "http://adfs.test.lab/adfs/services/trust"
set idp-single-sign-on-url "https://adfs.test.lab/adfs/ls/"
set idp-single-logout-url "https://adfs.test.lab/adfs/oauth2/logout"
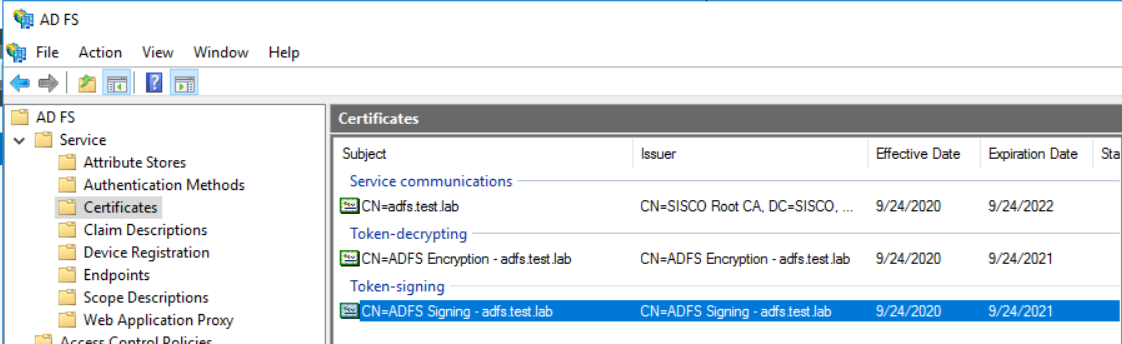
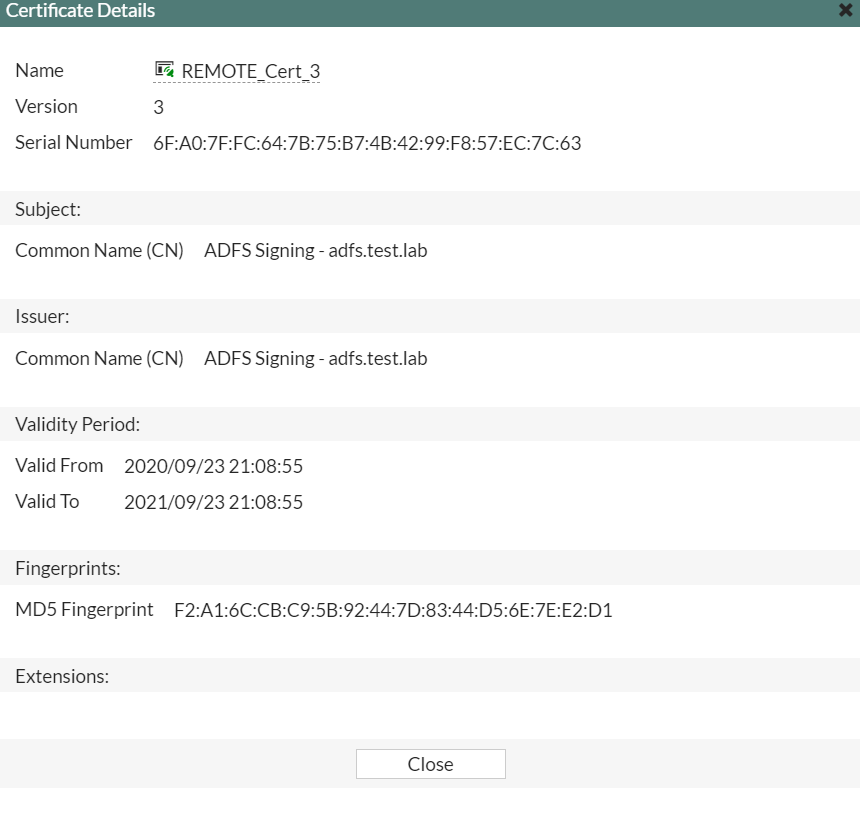
set idp-cert "REMOTE_Cert_3"
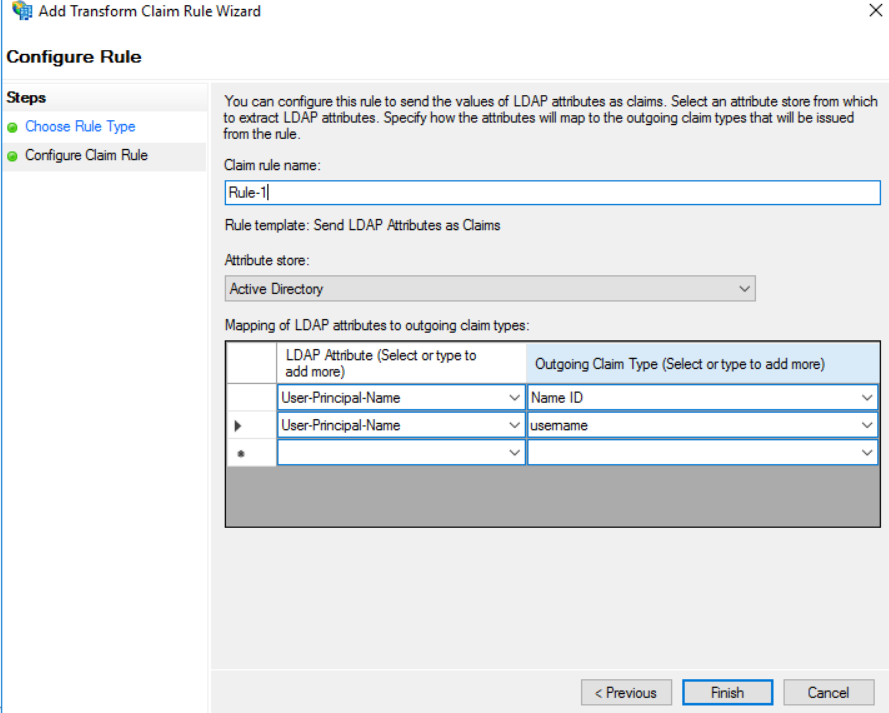
set user-name "username"
next
end
Configuration On ADFS:
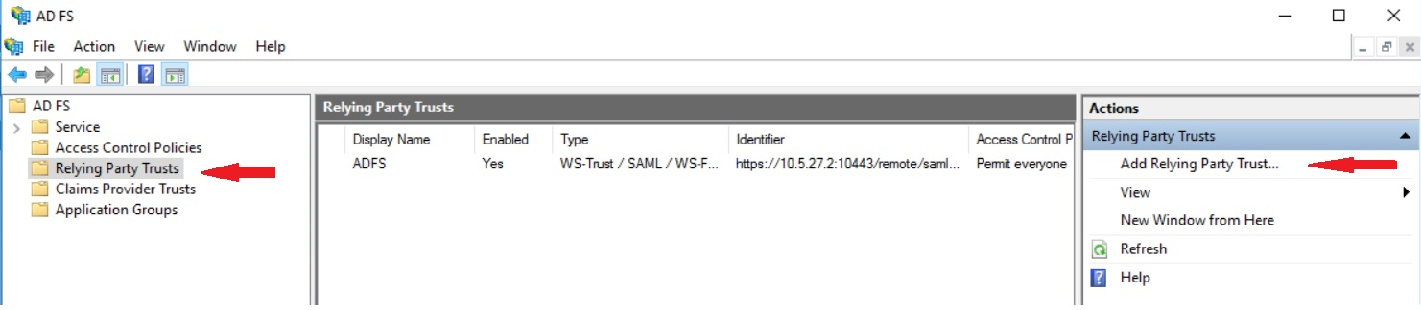
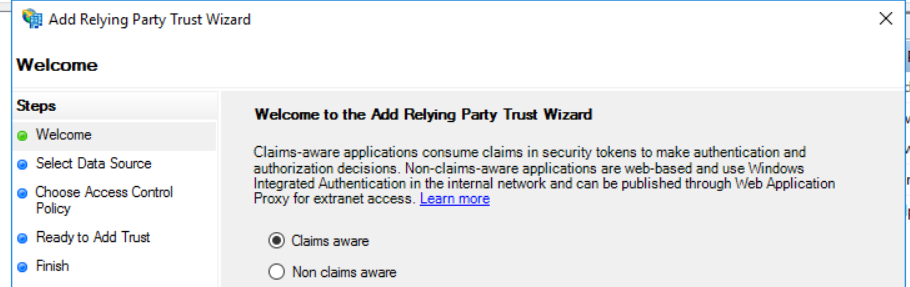
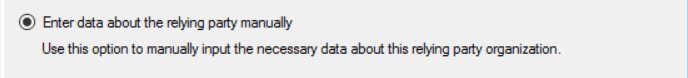
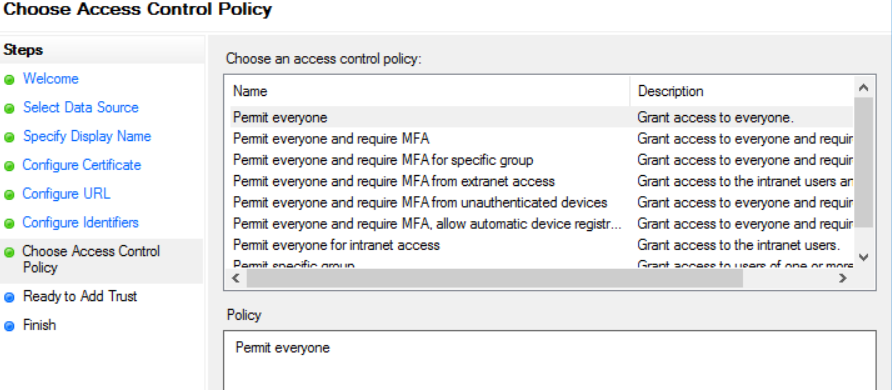
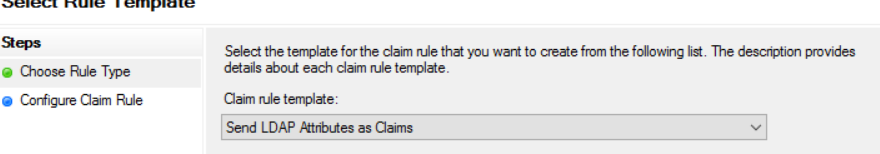
1) Open ADFS from Server Manager -> Tools -> AD FS Management and navigate to Relying Party Trusts and Add Relying Party Trust.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.