- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: HSTS enforcement
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Created on
04-18-2021
10:56 PM
Edited on
10-27-2023
02:20 AM
By
![]() Jean-Philippe_P
Jean-Philippe_P
Description
This article describes how to enable the HSTS for the admin login page.
The remote HTTPS server is not enforcing HTTP Strict Transport Security (HSTS).
The lack of HSTS allows downgrade attacks, and SSL-stripping man-in-the-middle attacks, and weakens cookie-hijacking protections.
Scope
From version 6.2.6.
Solution
From CLI.
config system global
set admin-hsts-max-age <value> <----- Range 0- 2147483647.
end
Note.
- HTTPS Strict-Transport-Security header max-age value in seconds. Meaning the number of seconds, the client should honor the HSTS setting.
- A value of 0 will reset any HSTS records in the browser. When admin-https-redirect is disabled the header max-age will be 0.
Verification.
- When the browser initiates the connection to the FortiGate, the unit will respond with the HSTS header for internal redirection.
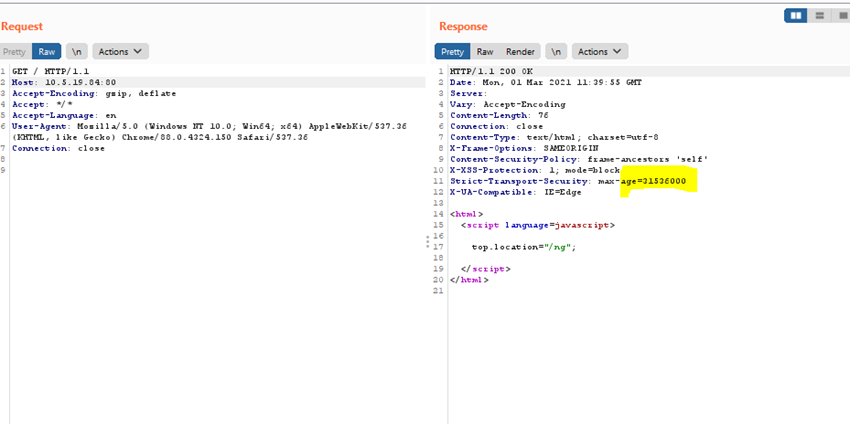
Enabling it will add an HSTS header to each HTTP response.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.