- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
FortiAnalyzer
FortiAnalyzer can receive logs and Windows host events directly from endpoints connected to EMS, and you can use FortiAnalyzer to analyze the logs and run reports.
- Fortinet Community
- Knowledge Base
- FortiAnalyzer
- Technical Tip: How to use FortiAnalyzer to detect ...
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
Scope
The custom Event Handler and Report provided can be used in FortiAnalyzer 6.4+.
Solution
This article describes how to use a custom Event Handler and Report in FortiAnalyzer to detect indicators attributed to the Kaseya VSA vulnerability. This vulnerability can be exploited for ransomware attack. See CVE-2021-30116 for reference.For more information on the threat, also see the FortiGuard Lab Threat Signal Report:What is included in Fortinet_SOC-Kaseya-Detection-v3.zip?1) Kaseya Ransomware Detection-v3.jsonThis event handler helps identify indicators detected by FortiGate's and FortiClient's IPS and Endpoint Vulnerability signatures. Logs triggering the event handler are generated from FortiGate and FortiClient. Therefore, their corresponding IPS and Endpoint Vulnerability signatures should be kept up to date to prevent and log the exploits.FortiGate: Ensure IPS Signature package is at least 18.112 or higher in order to cover Kaseya.VSA.Remote.Code.ExecutionFortiClient: Ensure Endpoint Vulnerability Protection is at least 1.250 or higher to cover Security Vulnerability cve-2021-30116 for Kaseya Server2) Kaseya_ransomware_detection_report-v3.datA report to summarize findings on activities related to the Kaseya VSA vulnerability, as detected by the AV and IPS Engine on FortiGate and FortiClient devices.See the Solution section for instruction on how to load the event handler into a FortiAnalyzer unit.
Scope
The custom Event Handler and Report provided can be used in FortiAnalyzer 6.4+.
Solution
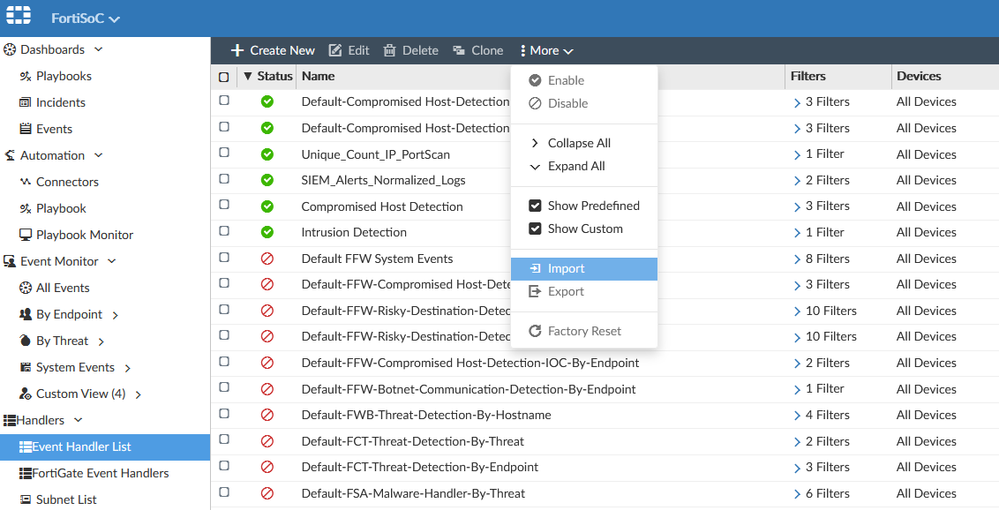
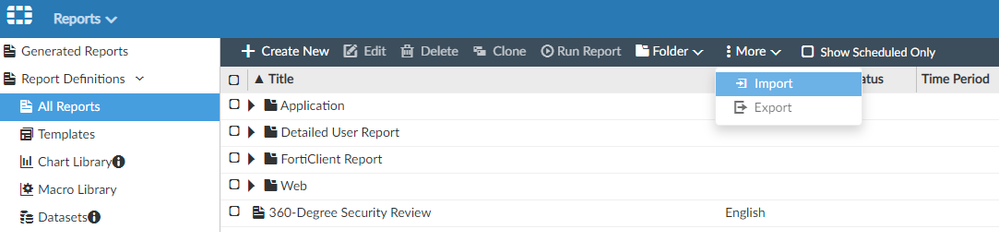
All screen shots provided below for illustration purposes are taken from FortiAnalyzer 6.4.4.1) Download the Fortinet_SOC-Kaseya-Detection-v3.zip file (contains 2 files)2) Unzip Fortinet_SOC-Kaseya-Detection-v3.zip3) Use Kaseya Ransomware Detection-v3.json to import into Event Handlersa. Choose an ADOM (if ADOMs are enabled)b. Choose the FortiSOC modulec. Select Event Handler Listd. Select the Import option under "More"e. Select Kaseya Ransomware Detection-v3.jsonResult: Kaseya Ransomware Detection-v3.json is enabled and will be triggered if the appropriate logs are received after after the event handler was imported4) Use Kaseya_ransomware_detection_report-v3.dat to import into Reportsa. Choose a Fabric ADOM (if ADOMs are enabled)b. Choose the Report modulec. Select the Import option under "More"d. Select Kaseya_ransomware_detection_report-v3.datResult: 'Kaseya_ransomware_detection_report-v3.dat' can be run anytime as determined by an admin user.
Labels:
Broad. Integrated. Automated.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Security Research
Company
News & Articles
Copyright 2024 Fortinet, Inc. All Rights Reserved.