- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: Configuring and troubleshooting Fir...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
This article describes how to configure and troubleshoot Firewall TAGs with FortiGate and FortiNAC.
Related documents:
- FortiNAC Endpoint connector - FortiGate new features.
- Fortinet security fabric FSSO integration guide.
Scope
FortiGate and FortiNAC Legacy.
Solution
- Log in to the FortiNAC GUI and go to System -> Settings -> System Communication Fortinet FSSO Settings.
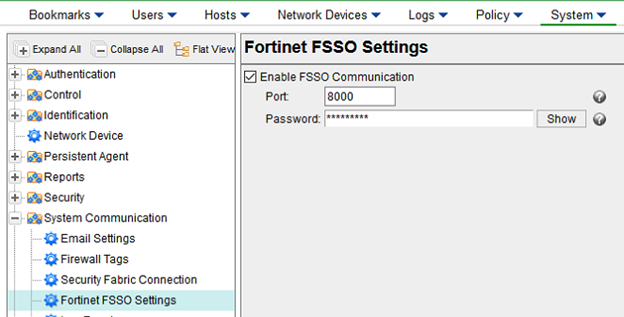
Ensure that the 'Enable FSSO Communication' box is checked and fill in the 'Password' field (see the below example):
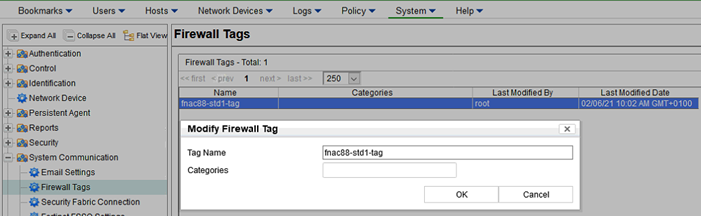
- Create 'Firewall Tags':
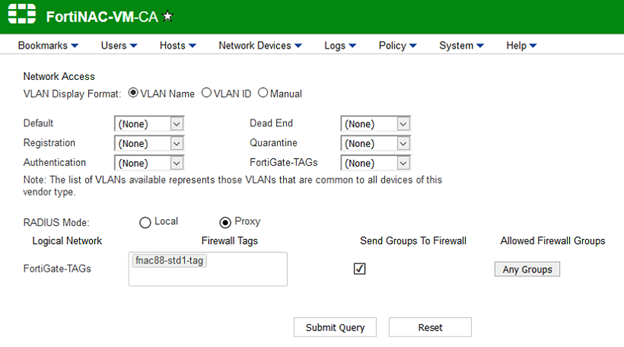
- Go to the 'Topology' view, select the FortiGate, select the 'Virtualized Devices' tab, and select the VDOM to enable 'Firewall Tags'. Then, enter the tag that was created in the previous step and select 'Submit Query':
- Add a FortiNAC Fabric Connector on the FortiGate:
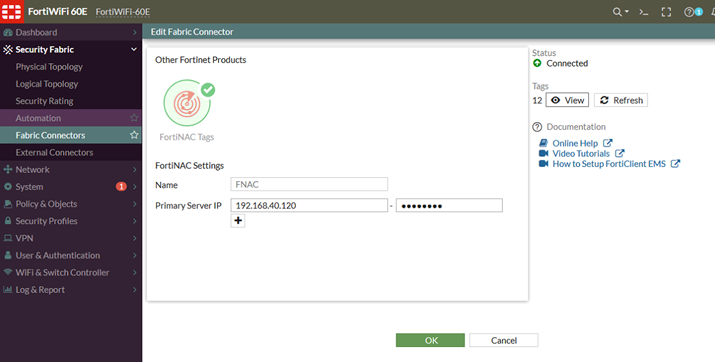
- Select 'Refresh' and select 'View':
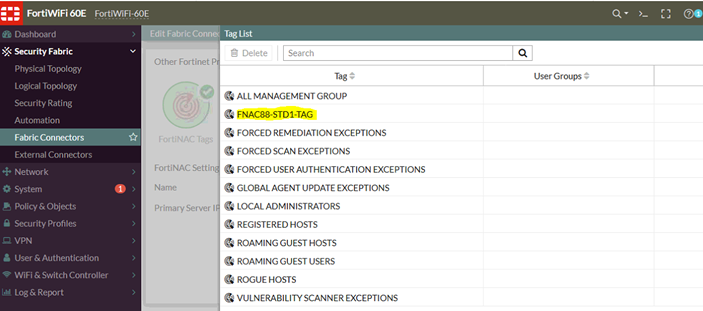
- If the tag that was created on FortiNAC is visible, use these tags in the firewall policies.
- To verify whether a TAG has been applied to a host and sent to FortiGate, use the following commands on FortiGate:
diag debug auth fsso list | grep x.x.x.x <- Replace x.x.x.x with the IP address from the host.
- Force the FSSO Tag to be sent from FortiNAC to FortiGate to work around cases where the VLAN is terminating on a Layer 3 device other than the FortiGate:
device -ip <IPaddress> -setAttr -name ForceSSO -value true
- Enable the following debug options and send the Putty session output to TAC support:
nacdebug -name DeviceInterface true
nacdebug -name SSOManager true
Device -ip <IPaddress> -setAttr -name DEBUG -value "ForwardingInterface TelnetServer"
- Reproduce the issue. Update the ticket with the timestamps and Username.
- After reproducing the issue, run the following command:
grab-log-snapshot
The script will collect and zip a large number of files.
This will take several minutes.
The resulting zip file (log-snapshot-<hostname>-<timestamp>.tar.gz) is located in /tmp directory.
See Technical Tip: How to get a debug log report from FortiNAC.
- Disable debugging:
nacdebug -name DeviceInterface false
nacdebug -name SSOManager false
Device -ip <IPaddress> -delAttr -name DEBUG -value "ForwardingInterface TelnetServer"
Verify which debugs are enabled:
nacdebug -all | grep -i true
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.