- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Technical Tip: How to configure an IPsec tunnel wi...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
| Description | This article describes how to configure an IPsec tunnel with Overlapping Subnets using vips. |
| Scope | FortiGate. |
| Solution |
This method is used as a workaround if changing the subnet is not possible. Only use this method as a last resort. 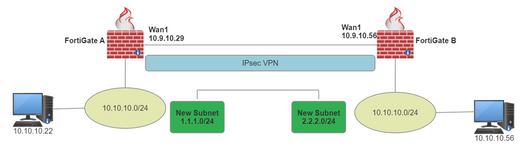

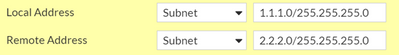
2) Create the new local Subnet for IPsec:

3) Create the new Remote subnet Address:

4) Change the local and remote subnet on the IPsec Phase 2 Selectors for the new subnet.
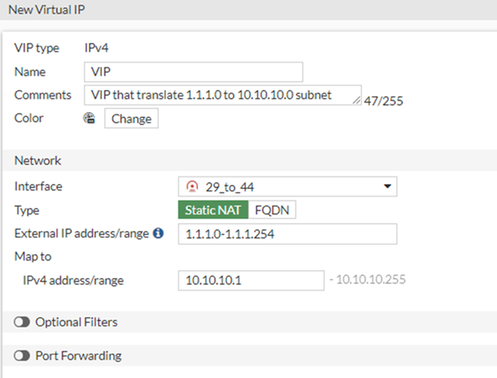
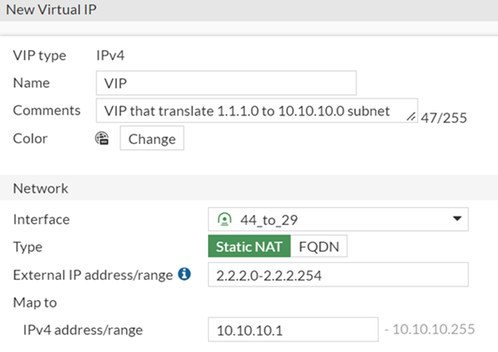
The purpose of this VIP is to translate traffic coming from 1.1.1.0 to the internal subnet 10.10.10.0
Otherwise, this can cause routing issues from Lan to Wan.
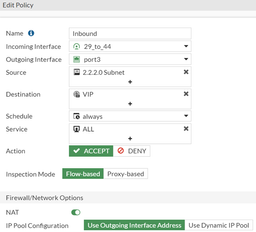
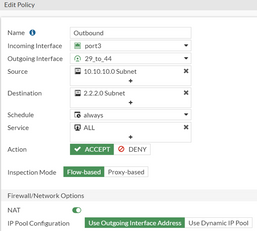
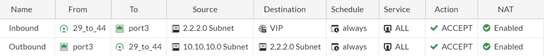
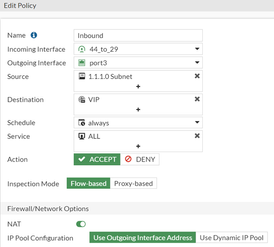
IP and an Outbound policy to Destination New remote subnet.
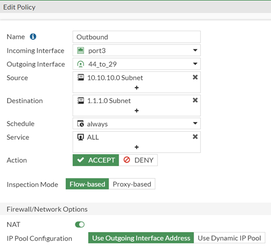
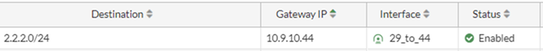 This route says that to reach 2.2.2.0/24, send the traffic over the IPSec tunnel.

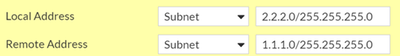
2) Create the new local Subnet for IPsec:

3) Create the new Remote subnet Address:

4) Change the local and remote subnet on the IPsec Phase 2 Selectors for the new subnet.
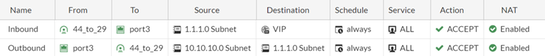
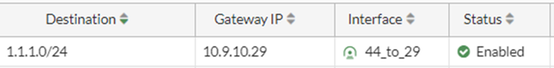
This route says that to reach 1.1.1.0/24, send the traffic over the IPsec tunnel. 
The same goes for Computer 10.10.10.56 who wants to communicate with computer 10.10.10.22. 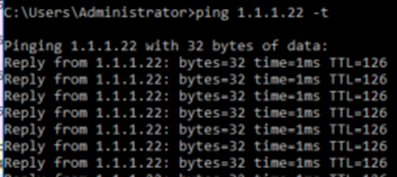
If the issue persists, contact Fortinet Support for more assistance. |
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.