- Forums
- Knowledge Base
- Customer Service
- FortiGate
- FortiClient
- FortiAP
- FortiAnalyzer
- FortiADC
- FortiAuthenticator
- FortiBridge
- FortiCache
- FortiCarrier
- FortiCASB
- FortiConnect
- FortiConverter
- FortiCNP
- FortiDAST
- FortiDDoS
- FortiDB
- FortiDNS
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiEDR
- FortiExtender
- FortiGate Cloud
- FortiGuard
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiMail
- FortiManager
- FortiMonitor
- FortiNAC
- FortiNAC-F
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPAM
- FortiPortal
- FortiProxy
- FortiRecon
- FortiRecorder
- FortiSandbox
- FortiSASE
- FortiScan
- FortiSIEM
- FortiSOAR
- FortiSwitch
- FortiTester
- FortiToken
- FortiVoice
- FortiWAN
- FortiWeb
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- ZTNA
- 4D Documents
- Customer Service
- Community Groups
- Blogs
- Fortinet Community
- Knowledge Base
- FortiGate
- Troubleshooting tip: How to troubleshoot ping pack...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
This article describes how to check if the ping drops are caused by FortiGate. When pinging an IP address, the PC sends an ICMP echo request and it shows successful if it receives the ICMP echo reply.
Scope
FortiGate.
Solution
Network Topology:
PC connecting to Fortigate SSLVPN [198.18.0.177] -> Internet -> [198.18.0.117] Fortigate [10.218.0.117]
PC SSLVPN Tunnel IP address: 10.212.134.200
PC Public IP address: 198.18.0.177
Fortigate LAN IP address: 10.218.0.117
- Perform a simultaneous packet capture on 2 CLI sessions. Encrypted traffic from PC to FortiGate:
diag sniffer packet any 'host <PC Public IP address> and port <SSLVPN Port>' 4 0 l
Decrypted traffic:
diag sniffer packet any 'host <Fortigate LAN IP address> and host <SSLVPN Tunnel IP address>' 4 0 l
- Ping the FortiGate LAN IP address from the PC connected with SSL VPN. No other traffic must be sent on the SSL VPN Tunnel.
- It is possible to check the ICMP echo request and reply with the packet size and the timestamp. The screenshot below shows when there is no packet drop:
Encrypted traffic from PC to FortiGate:
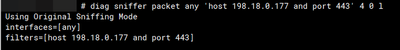
diag sniffer packet any 'host 198.18.0.177 and port 443' 4 0 l
Using Original Sniffing Mode
interfaces=[any]
filters=[host 198.18.0.177 and port 443]
2024-01-23 12:51:17.817090 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 56
2024-01-23 12:51:18.638540 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 107 <----- ICMP echo request in
2024-01-23 12:51:18.638720 port4 out 198.18.0.117.443 -> 198.18.0.177.53810: udp 56
2024-01-23 12:51:18.638993 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 75
2024-01-23 12:51:18.639372 port4 out 198.18.0.117.443 -> 198.18.0.177.53810: udp 107 <----- ICMP echo reply out
2024-01-23 12:51:19.648938 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 107
2024-01-23 12:51:19.649081 port4 out 198.18.0.117.443 -> 198.18.0.177.53810: udp 107
2024-01-23 12:51:20.660098 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 107
2024-01-23 12:51:20.660220 port4 out 198.18.0.117.443 -> 198.18.0.177.53810: udp 107
2024-01-23 12:51:21.671228 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 107
2024-01-23 12:51:21.671357 port4 out 198.18.0.117.443 -> 198.18.0.177.53810: udp 107
2024-01-23 12:51:31.672388 port4 in 198.18.0.177.53810 -> 198.18.0.117.443: udp 56
2024-01-23 12:51:35.676054 port4 out 198.18.0.117.443 -> 198.18.0.177.53810: udp 56
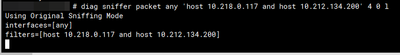
Decrypted traffic:
diag sniffer packet any 'host 10.218.0.117 and host 10.212.134.200' 4 0 l
Using Original Sniffing Mode
interfaces=[any]
filters=[host 10.218.0.117 and host 10.212.134.200]
2024-01-23 12:51:18.638614 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-23 12:51:18.638633 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
2024-01-23 12:51:19.649010 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-23 12:51:19.649029 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
2024-01-23 12:51:20.660168 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-23 12:51:20.660187 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
2024-01-23 12:51:21.671300 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-23 12:51:21.671322 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
- An example of a packet capture where there is a ping drop seen on the PC. This is caused by the DOS Policy on FortiGate:
2024-01-22 14:10:16.303841 port1 in 198.18.0.177.64826 -> 198.18.0.117.443: udp 107
2024-01-22 14:10:16.303877 port1 out 198.18.0.117.443 -> 198.18.0.177.64826: udp 107
2024-01-22 14:10:17.309418 port1 in 198.18.0.177.64826 -> 198.18.0.117.443: udp 107
2024-01-22 14:10:17.309443 port1 out 198.18.0.117.443 -> 198.18.0.177.64826: udp 107
2024-01-22 14:10:18.325634 port1 in 198.18.0.177.64826 -> 198.18.0.117.443: udp 107 <----- Traffic coming in but not seen on the decrypted traffic.
2024-01-22 14:10:23.307584 port1 in 198.18.0.177.64826 -> 198.18.0.117.443: udp 107 <----- Traffic coming in but not seen on the decrypted traffic.
2024-01-22 14:10:28.303249 port1 in 198.18.0.177.64826 -> 198.18.0.117.443: udp 107 <----- Traffic coming in but not seen on the decrypted traffic.
2024-01-22 14:10:28.303331 port1 out 198.18.0.117.443 -> 198.18.0.177.64826: udp 107
2024-01-22 14:10:29.317200 port1 in 198.18.0.177.64826 -> 198.18.0.117.443: udp 107
2024-01-22 14:10:16.303859 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-22 14:10:16.303866 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
2024-01-22 14:10:17.309427 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-22 14:10:17.309435 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
2024-01-22 14:10:28.303268 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-22 14:10:28.303275 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
2024-01-22 14:10:29.317211 ssl.root in 10.212.134.200 -> 10.218.0.117: icmp: echo request
2024-01-22 14:10:29.317218 ssl.root out 10.218.0.117 -> 10.212.134.200: icmp: echo reply
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
Copyright 2024 Fortinet, Inc. All Rights Reserved.